Blog

June 27, 2025 •9 min read • Ai
Efficient Research in Cybersecurity — How AI Tools Streamline CIS Hardening Analysis

February 11, 2025 •9 min read • Agile
Embracing Agile to Foster Self-Organization in Cybersecurity Teams

February 9, 2025 •4 min read • Vm
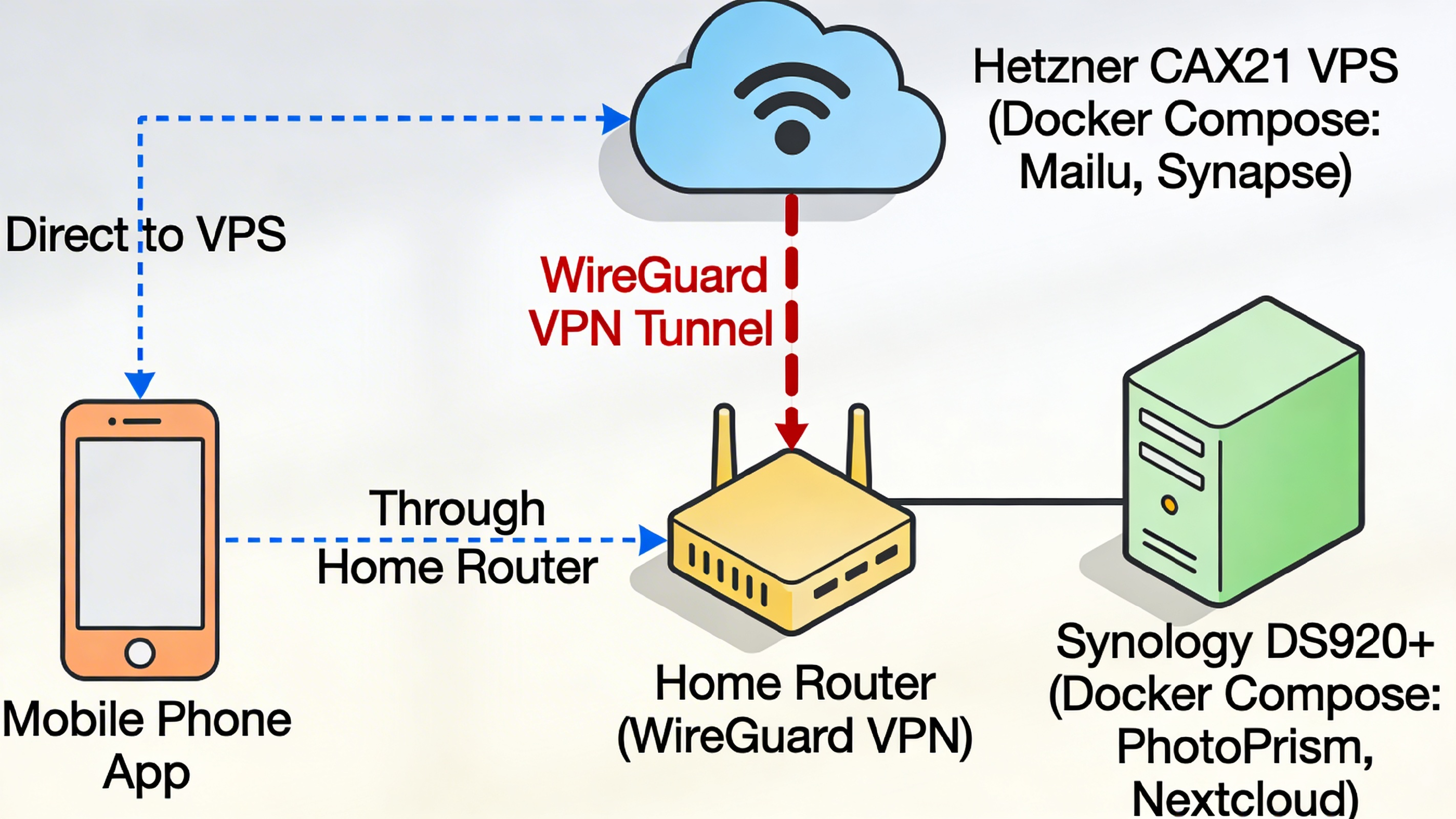
How I Moved My Synology DS920+ VM to an External SSD (And Survived to Tell the Tale)

February 6, 2025 •5 min read • Ai
Dockerizing Fabric - A Comprehensive AI Augmentation Setup

May 30, 2024 •4 min read • Selfhosted
Hosting Matomo with Docker Compose: A Step-by-Step Guide

May 29, 2024 •5 min read • Selfhosted
Hosting Home Assistant with Docker Compose: A Step-by-Step Guide
February 5, 2021 •3 min read • Cybersecurity
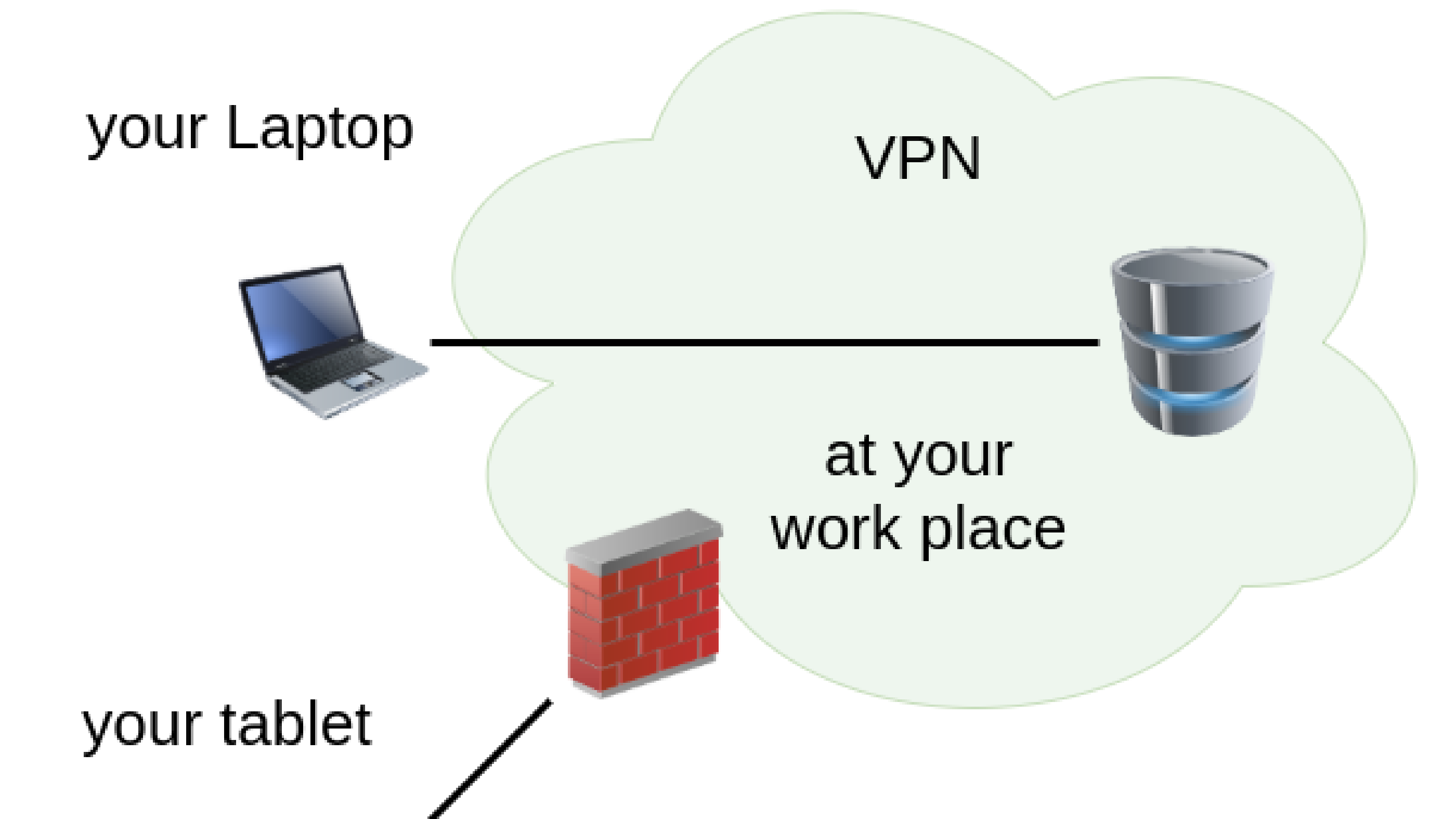
VPNs: When to use a Virtual Private Network

September 16, 2020 •4 min read • Hacking
Enumeration of your Web Servers