Reverse Engineer the EasyPass Challenge
Posted on August 27, 2020 • 3 min read • 583 words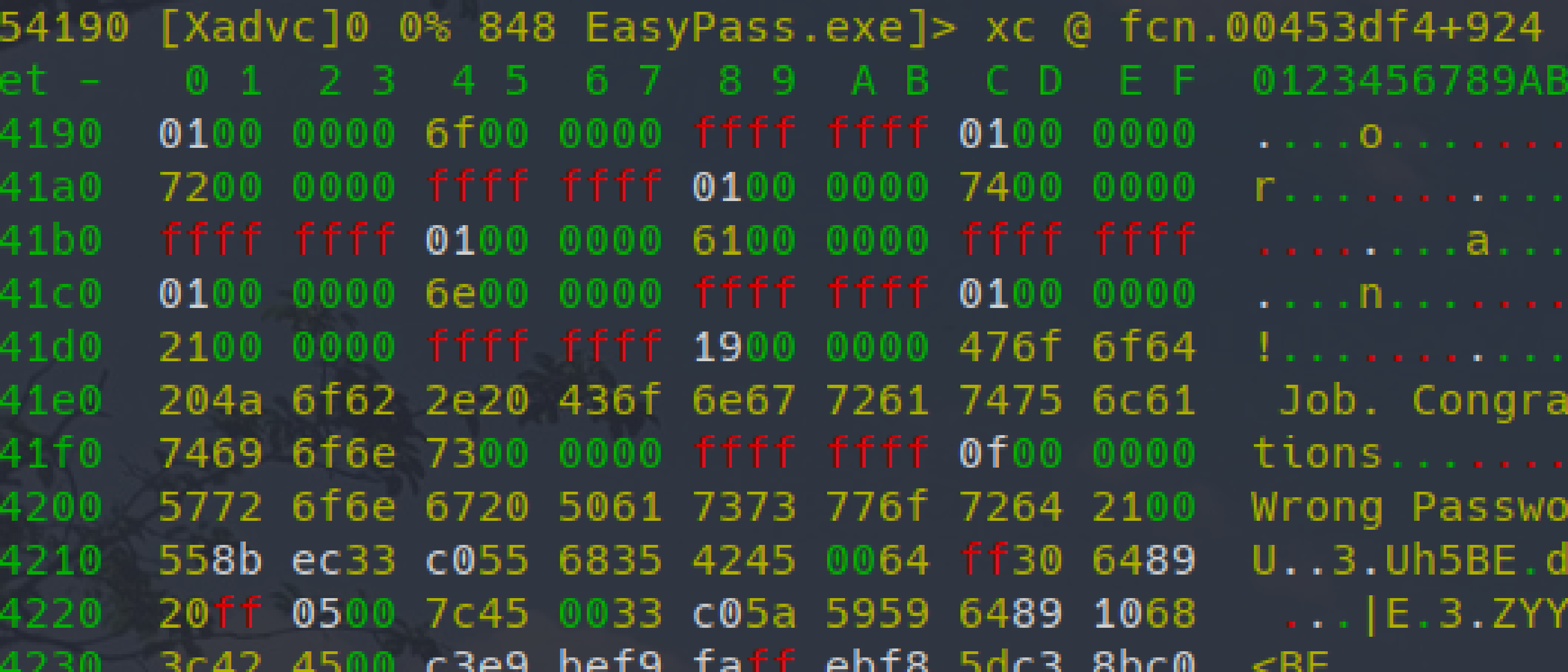
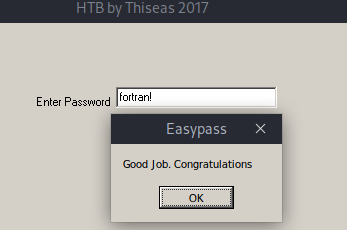
In this short tutorial, we will see how to use radare2 to reverse engineer the EasyPass challenge from HTB. Let’s start by looking what the program does.
So, let’s load up the binary in r2.
r2 EasyPass.exeNow, we are ready to start our analysis using reverse engineering. First, let radare2 do the difficult job of analyzing the program structure and discovering functions.
peter@terra> r2 EasyPass.exe
-- Your problems are solved in an abandoned branch somewhere
[0x00454450]> aav
[x] Finding xrefs in noncode section with anal.in=io.maps
[x] Analyze value pointers (aav)
[x] Value from 0x00454600 to 0x00455000 (aav)
[x] 0x00454600-0x00455000 in 0x454600-0x455000 (aav)
[x] 0x00454600-0x00455000 in 0x401000-0x454600 (aav)
[x] Value from 0x00401000 to 0x00454600 (aav)
[x] 0x00401000-0x00454600 in 0x454600-0x455000 (aav)
[x] 0x00401000-0x00454600 in 0x401000-0x454600 (aav)
[0x00454450]> s entry0Finding the right place
Well, we are now at the entry point of the program. However, this program will at startup only construct the window and draw it to the display. That’s something we are not really interested in. We are looking for the password check. So, let’s try to find this section by searching for strings in the binary which contain the string Password.
[0x004540e1]> izz | grep Pass
2814 0x0002a105 0x0042ad05 13 14 CODE ascii \fPasswordChar
5490 0x00053600 0x00454200 15 16 CODE ascii Wrong Password!
7078 0x000622ad 0x004682ad 14 15 .rsrc ascii Enter Password
7090 0x0006232e 0x0046832e 23 24 .rsrc ascii Check Password\bTabOrderAs „Wrong Password” was the text on the message we got with our wrong trial, this might be a good starting point.
[0x00454450]> s 0x454200Let’s switch into the visual mode V and have a look what we find at this position. You can use p or P to cycle between different views.
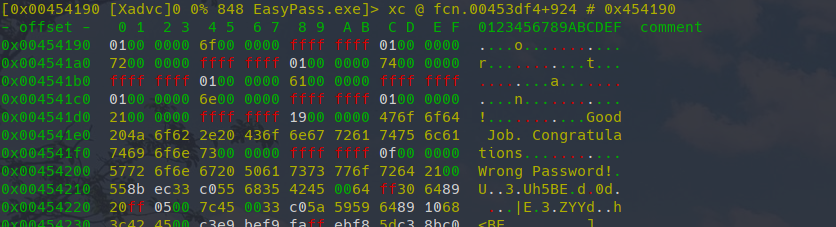
Hence, we search for “Good” and note its location. Now, we have already seen that we are actually in a data section of the binary which only contains string, no code. Hence, we must find the point of code which references this string.
[0x004541dc]> axt 0x4541dc
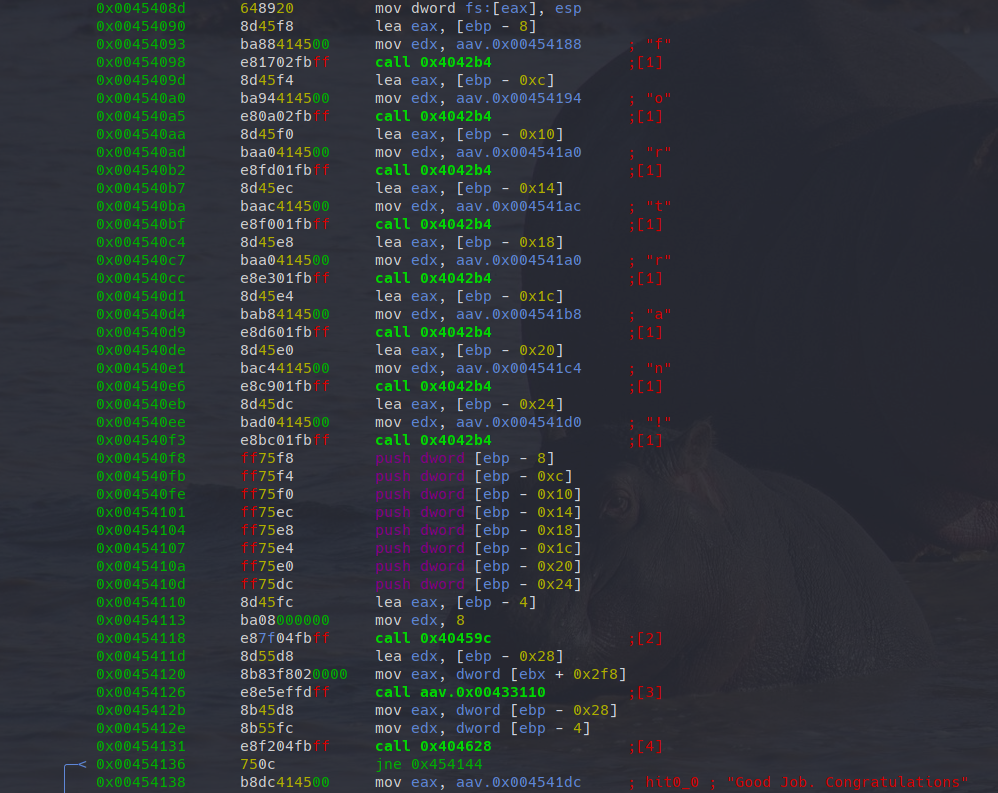
(nofunc) 0x454138 [DATA] mov eax, 0x4541dcWith axt (A cross(X)-reference To) we find this location. Let’s again jump into the visual mode and have a look at the disassembly.
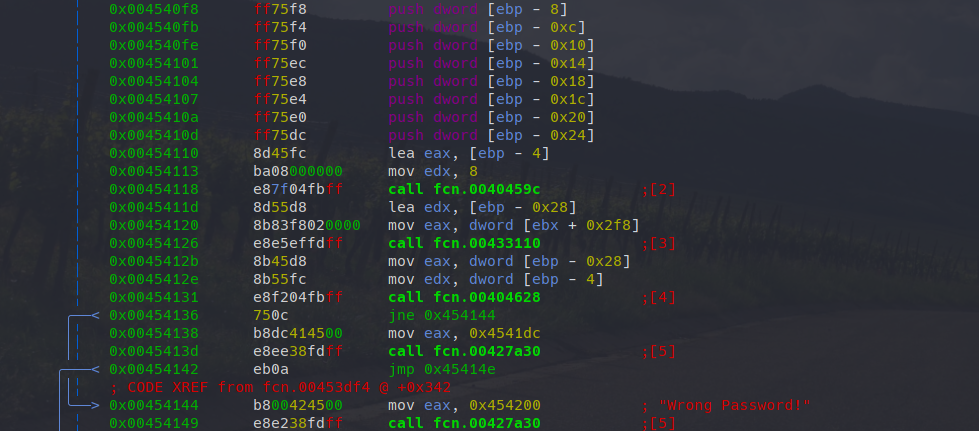
Understanding the challenge
There are two times calls to fcn.00427a30. The second one in the last row and the first row some rows before. In both cases immediately before these function calls, an address to a string is written to eax. radare2 was able to identify the last string (“Wrong password”), while we also already know the address for the first call. It’s the address we found for the “Good job“ string. So, the interesting point is now to understand when is which part called. Right before the first mov+call sequence, there is a comparison jne which would skip the “Good job“ string. You can see this by the drawing radare2 made for us or by having a look on the jump address. Scrolling just a bit further up, we see a series of calls to the same function (at 0x4042b4) and the xref lookup in the beginning (aav) also dereferenced some characters for us. Do we already have our password?